Is Cyber Security Hard? Expert Guidance Makes It Easy [2025]
Education ranks as the top target for hackers worldwide, with almost 2,300 attacks every week. Does your institution struggle with cyber security implementation? Many others ask this same question, especially since ransom demands now reach a massive $3.65 million in 2023.
Cybersecurity has dominated higher education institutions’ risk registers for three straight years. Attacks have surged by 258% between 2021-22 and 2022-23. K-12 districts face similar threats. Cyber crimes tripled during the pandemic, and school districts now face at least one incident each school day. A full picture of cybersecurity risks and practical cloud security tips can reduce these risks by a lot.
We break down why cybersecurity feels so overwhelming in this piece. The text addresses ground challenges behind the question “is cybersecurity hard?” and offers expert guidance that simplifies the process. You’ll find concrete steps to boost your institution’s defenses in 2025. This approach works even without advanced technical knowledge or stretching your limited resources.
Why Cybersecurity Feels Overwhelming
Cybersecurity implementation feels like solving a puzzle where pieces keep changing. The answer to “is cyber security hard?” comes down to three big challenges that make it complex.
Lack of clear starting points
Getting started in cybersecurity can be overwhelming. New professionals find it hard to create a well-laid-out learning path with so many career options, certifications, and technical skills. They face a tough situation – you need experience to get hired, but you need a job to build experience. Companies keep looking for qualified candidates. The choice between becoming a security generalist, network engineer, or picking from many other specializations leaves newcomers stuck on their first step.
Too many tools and frameworks
About 72% of organizations use multiple security vendors, which creates operational strain. Security professionals (43%) say their security stacks are too complex and take too much time to maintain. This leads to 42% of organizations going over budget due to duplicate solutions. Another 41% can’t properly automate their security processes because their tools don’t work together well. The mix of different technologies creates gaps in security – 39% of organizations can’t see threats consistently because data from different vendors doesn’t blend together.
Shortage of skilled professionals
The talent shortage might be the biggest problem right now. Global cybersecurity workforce needs exceeded 4 million in 2023 (ISC²), often cited as a growing gap that continues to widen annually. The United States alone needs 225,200 skilled cybersecurity workers. Jobs that ask for 2+ years of experience have only 77% of the workers needed. Entry-level positions have 12% more workers than needed, but 90% of organizations still say their security teams lack skills. This happens because employers want experienced professionals – only 7% of cybersecurity workers come straight from educational programs.
These challenges show us where to start making cybersecurity more approachable, especially at the time you need to do a cybersecurity risk assessment or learn about cloud security tips.
The Real Challenges Behind ‘Is Cybersecurity Hard?’
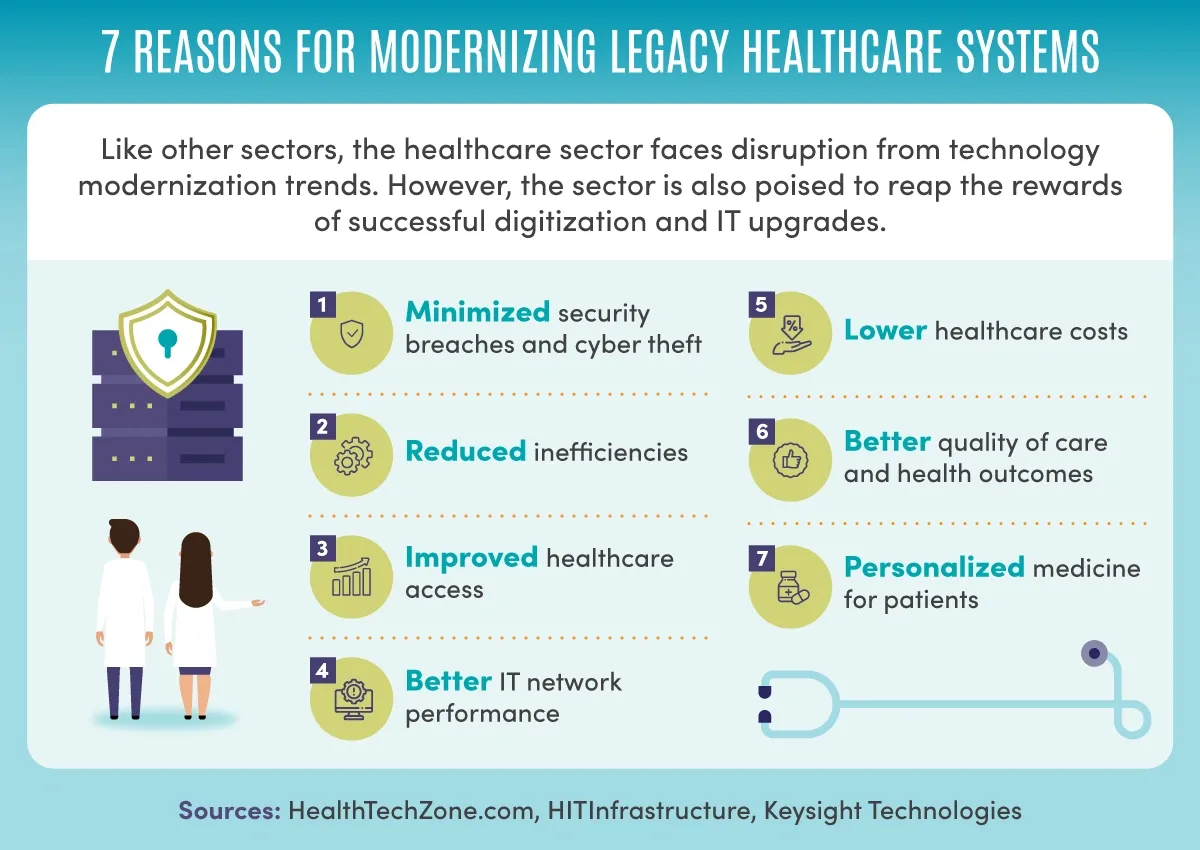
Image Source: Maryville Online – Maryville University
Organizations face deeper structural problems with cybersecurity beyond the original confusion. The reality shows that good protection needs more than just technical expertise.
Complex IT environments and legacy systems
The interconnection of billions of devices creates endless dependencies that make security harder. Modern IT systems keep growing with new apps, databases, and infrastructure. They switch between cloud and local solutions and generate huge amounts of data. Many companies still depend on old systems without security updates, which makes them easy targets for cyberattacks. These outdated platforms don’t have the features needed for advanced security. This creates dangerous holes in defense systems.
Cultural resistance and user non-compliance
Bad security culture hurts enterprise safety more than technical limits. Simple awareness programs or security training can’t protect organizations well enough. Security must become part of company values and practices to work. Staff often see security measures as annoying or invasive. People tend to hide weak spots when they fear punishment for mistakes. This gives attackers the chance they need.
Budget constraints and staffing shortages
Money limits stand as the biggest problem for security projects. 54% of cyber leaders say budget constraints stop them from doing what’s needed. Security budget growth fell to 4% in 2025 – the lowest in five years. The share of IT spending on security dropped from 11.9% to 10.9%. Companies spend only 9% of their IT money on cybersecurity. This falls well below the ideal 12%.
Cybersecurity risk assessment is often skipped
Companies often ignore this basic foundation of modern cyber protection. Security becomes scattered and fails without proper risk review. A full assessment looks at threats, weak points, critical assets, and business effects. This gives useful information to match controls with real risks instead of guessing. Many companies struggle to build good protection plans because they don’t understand the real dangers they face.
How Expert Guidance Simplifies the Process
Expert frameworks and tools help organizations manage cybersecurity effectively, regardless of their resource limitations. Good guidance brings structure to what seems like an overwhelming field at first glance.
Understanding the NIST and CIS frameworks
The NIST Cybersecurity Framework uses five key functions; Identify, Protect, Detect, Respond, and Recover, that simplify cybersecurity implementation. Both technical and non-technical stakeholders can understand this structure thanks to its clear, outcome-based language. The CIS Controls provide a prescriptive, prioritized set of best practices that boost your cybersecurity posture. These controls create a path to comply with regulations like PCI DSS, HIPAA, and GDPR. Organizations can adopt multiple approaches without duplicating efforts since both frameworks work together seamlessly.
Using automation to reduce manual workload
Daily cybersecurity maintenance presents significant challenges. Automation helps by monitoring network anomalies, identifying inappropriate user activity, and speeding up incident response. 42% of organizations struggle with security process automation because their tools don’t integrate well. The right automation solutions can turn tedious manual tasks into quick, consistent processes.
Cloud security tips for modern institutions
CISA and NSA recommend five crucial practices for cloud environments. Organizations should implement secure identity and access management, use proper key management, establish network segmentation with encryption, secure data, and reduce risks from managed service providers. Cloud storage configuration needs verification during deployment.
What is data leakage protection and why it matters
Data leakage protection stops sensitive information from being shared or used unsafely. This technology keeps an eye on data across on-premises systems, cloud locations, and endpoint devices. Organizations can achieve compliance with HIPAA and GDPR regulations while gaining visibility into their data flow. Data leaks often stem from negligence or poor security procedures. That’s why DLP should be a cornerstone of your security strategy.
Steps to Make Cybersecurity Easier in 2025
Making cybersecurity manageable instead of overwhelming requires a structured approach. These practical steps will help you build stronger defenses without straining your team or budget.
Start with a cybersecurity risk assessment
A detailed risk assessment serves as the foundation of effective security. This process helps you identify threats to your operations, vulnerabilities in your systems, and potential risks. Regular assessments will give you a baseline of cybersecurity measurements that show your progress. The assessment should review both internal and external threats to determine which assets face risks and what controls already exist.
Choose a framework that fits your needs
Your choice of cybersecurity framework depends on several factors like business objectives, regulatory requirements, and available resources. The NIST Cybersecurity Framework stands as the gold standard to assess cybersecurity maturity and identify security gaps. ISO 27001 shows stakeholders you’re implementing proper cyber risk management for international operations. Remember that frameworks don’t offer one-size-fits-all solutions.
Train staff and students on simple hygiene
People make mistakes that create security vulnerabilities. Your first line of defense grows stronger through regular training on phishing attempts, strong passwords, suspicious incident reporting, and software updates. Document cybersecurity policies that promote good habits like avoiding public Wi-Fi, using multi-factor authentication, and backing up data weekly. Join hundreds of students who’ve mastered cyber security with us!
Automate where possible to save time and cost
Security automation cuts down manual effort by using technology to handle repetitive security tasks. This makes:
- Faster threat detection and incident response
- Improved productivity among security analysts
- Standardization of security processes across the organization
Your team can focus on complex, strategic challenges that need expert judgment.
Monitor and update systems regularly
Budget-friendly protection against cyber threats starts with keeping software and systems current. Turn on automatic updates for operating systems and applications when available. Schedule weekly manual checks for systems without automatic updates. Replace any software that no longer receives security updates. System monitoring helps your cybersecurity measures stay effective against new threats.
Conclusion
Cybersecurity poses significant challenges to educational institutions, especially when attacks rose by 258% between 2021-22 and 2022-23. The question “Is cybersecurity hard?” becomes easier to answer if you break it into manageable parts. Complex IT environments, cultural resistance, and budget constraints create ground obstacles, yet organizations can overcome these with the right approach.
Expert frameworks like NIST and CIS create clear pathways that turn cybersecurity from an overwhelming concept into practical steps. Your institution can focus on concrete actions instead of feeling overwhelmed by talent shortages or tool overload. These actions include risk assessments, framework selection, staff training, and automation implementation where possible.
The digital world keeps changing, so monitoring and updates are vital to maintain strong defenses. Your educational institution can build reliable protection even with limited resources by understanding core concepts like data leakage protection.
Join hundreds of students who’ve mastered cyber security with us! Their success shows that cybersecurity becomes available to everyone with proper guidance, regardless of technical background.
Threats to educational institutions will persist, but your defense grows stronger with each security measure you implement. Cybersecurity brings its challenges, but your institution can reduce risks while working within resource limits through structured approaches and expert guidance. Remember, effective cybersecurity isn’t about perfection, it focuses on continuous improvement and resilience against evolving threats.
![Is Cyber Security Hard Expert Guidance Makes It Easy [2025]](https://skylineacademic.com/wp-content/uploads/2025/10/is-cyber-security-hard-expert-guidance-makes-it-easy-1024x536.png)
![Is Cyber Security Hard Expert Guidance Makes It Easy [2025]](https://skylineacademic.com/wp-content/uploads/2025/10/is-cyber-security-hard-expert-guidance-makes-it-easy.png)